Selecting the right servers for your business is extremely important and can either promote optimal performance, reliability, and security of your business computing; or it can present nothing but problems. Today, we will go through six tips to help you make good decisions about servers for your business.
Indevtech Blog
The cloud is one of the most valuable tools available to modern businesses, but the extent to which organizations utilize it will vary depending on their specific needs. For example, some organizations might be fine with the limited control offered by the public cloud, but others might need more dynamic features and control over their data with a private cloud. We’ll help you determine which is right for you, as well as some of the specific considerations needed for a private cloud solution.
It is little wonder that, with millions of businesses relying on their secure servers for a variety of computing needs, that Microsoft reigns supreme in profitability. In order to maintain this status, Microsoft must make sure that their software is properly cared for and supported - or retired if these titles are no longer practical to maintain. SQL Server 2008 and SQL Server 2008 R2 are soon due for the chopping block, with an official retirement date of July 9, 2019.
It is impossible to understate the importance of a server to today’s businesses. We talk a big game as to how important data is, but we don’t often broach the topic of how important it is to ensure that your server is well-maintained. Below, we discuss how to determine what your servers need for optimal performance, and how you can be sure that they get it.
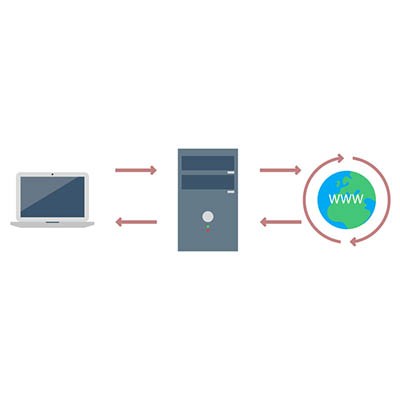
Your server room may be somewhat intimidating to consider. Wires everywhere, mechanical boxes that just sit there, lights blinking intermittently, and the distinct feeling that you probably shouldn’t touch anything - not even a proxy server, whatever that is. However, to help you get to know your tech, the proxy server is exactly what we discuss below!
You don’t have time to worry about managing your email solution, but it’s still a vital aspect of your business’s operations. You never know when someone will fall for a spam message, and you certainly can’t look over the shoulders of each employee to make sure they don’t. What’s the busy business owner to do? How can you get quality email management without it eating up too much time and effort on your part?
When a business undergoes a hardware refresh, it often comes saddled with unexpected costs and downtime. This is sometimes caused by hardware failure, or from unplanned-for data migration. With the advent of virtualized servers, businesses now have a better way to recover from the woes of server refreshes. Rather than purchase new hardware, it’s more economically viable to go with a virtual server that’s hosted in the cloud.
 Do you know which database management system is used by your company’s servers? Obviously your end users aren’t expected to know the answer to this question, but this is something that you, as a business owner, need to be aware of. If you don’t keep track of which database software you’re using, you might accidentally wait too long and wind up running an unsupported piece of software. For example, you need to move away from SQL Server 2005 (which is now unsupported) as soon as possible.
Do you know which database management system is used by your company’s servers? Obviously your end users aren’t expected to know the answer to this question, but this is something that you, as a business owner, need to be aware of. If you don’t keep track of which database software you’re using, you might accidentally wait too long and wind up running an unsupported piece of software. For example, you need to move away from SQL Server 2005 (which is now unsupported) as soon as possible.
 Technology, while a great asset that can be leveraged for your benefit, can also frighten businesses due to how unpredictable it can be at times. The constant threat of data loss, identity theft, and hardware failure can cripple your business’s ability to retain operations. Specifically, businesses can learn about risk management by analyzing the processes used by an industry where risk management is absolutely critical: nuclear power plants.
Technology, while a great asset that can be leveraged for your benefit, can also frighten businesses due to how unpredictable it can be at times. The constant threat of data loss, identity theft, and hardware failure can cripple your business’s ability to retain operations. Specifically, businesses can learn about risk management by analyzing the processes used by an industry where risk management is absolutely critical: nuclear power plants.
 With the United States’ Presidential election ramping up, it’s hard to go anywhere without seeing Hillary Clinton’s face. The former U.S. secretary of state and first lady, Clinton is making her second attempt at the Presidency. She has gained some negative attention recently in regards to emails she had sent from a personal email address when she was the United States’ top diplomat and it’s opened up some questions about data security at the highest reaches of government.
With the United States’ Presidential election ramping up, it’s hard to go anywhere without seeing Hillary Clinton’s face. The former U.S. secretary of state and first lady, Clinton is making her second attempt at the Presidency. She has gained some negative attention recently in regards to emails she had sent from a personal email address when she was the United States’ top diplomat and it’s opened up some questions about data security at the highest reaches of government.