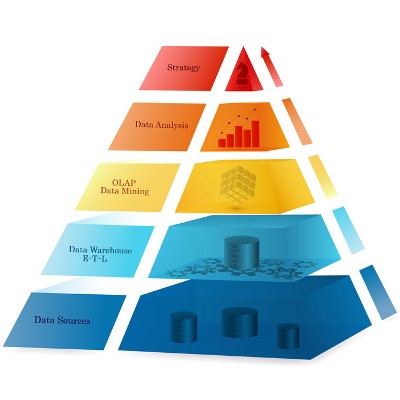
The modern business creates and deals with a lot of data, and has for some time. For most of that time, this data has just been ignored, but recent developments in analytics and business intelligence has made this data extremely valuable. In order for your analysts to make accurate determinations they’ll need access to a wide variety of data from a myriad of sources. This is where data warehousing comes in.
Indevtech Blog
How do you look at your organization’s data? The answer will likely be the same as how you look at your organization. The businesses that do more to use their data to improve their business’ process, policies, and strategies, are the businesses that, by-in-large, are the ones that grow more rapidly and see more operational efficiency. This month, we thought we would look at four ways your business can use their data to actively improve its operations.
2017 saw the rise of many great technology solutions for small business, including an explosion of popularity in business intelligence, artificial intelligence applications, and machine learning. Meanwhile, other established technologies have continued their domination of the industry. What can your organization look forward to seeing on the forefront of the small business technology race in 2018?