AI has been one of the leading innovative topics to hit the technology world over the past couple of years. At first, people thought that AI was only the process of creating machines that will inevitably destroy the human race, and didn’t understand that algorithmic machine learning could have stark benefits for business and society. Today, AI can be found in all types of different pieces of software. Let’s take a look at a couple of ways AI is currently being used in business.
Indevtech Blog
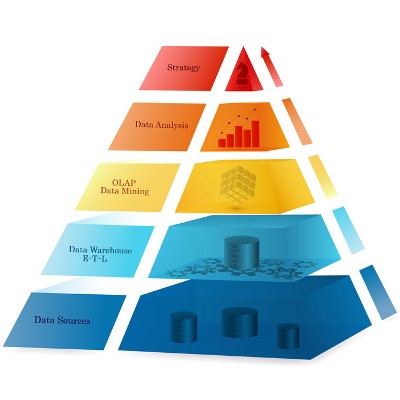
Today, large companies typically use their data to help them make more educated business decisions. This strategy can actually benefit smaller businesses as well. However, they often don’t think they have enough data to facilitate analytics or BI (Business Intelligence) platform. Let’s take a look at how small businesses can use their big data.
It’s not always easy to identify what will be hip and trendy years from now, but big data is attempting to bridge this gap. In general, due to the unpredictability of human behavior, it can be difficult to spot cultural anomalies before they happen. Despite these challenges, algorithms are being applied to various practices in both the business world and elsewhere. One innovative way in which it’s being used is by attempting to predict the next bestselling novel.